Azure AD App registrations provides ways for authenticating
or authorizing the user custom applications which uses Azure AD, to access the
data available on the Microsoft products/services.
Why Azure AD App Registration? You might have already worked
with custom applications that uses Azure Control Service, which provides way
for authenticating users to gain access to web applications and services. As
ACS is getting deprecated, Microsoft provides ways for authenticating the
applications and provides way for enabling permissions for users to access the
data.
 |
| (Source: https://cloudblogs.microsoft.com/enterprisemobility/2013/06/22/azure-active-directory-is-the-future-of-acs/) |
The following method is one way for registering the custom
built applications and authenticating users for accessing Microsoft services.
1. Azure AD has options for registering the user custom
applications, where users can provide the app details like app name,
application type (web or native app) and sign-on page URL. This helps
authenticating users for accessing the application data.
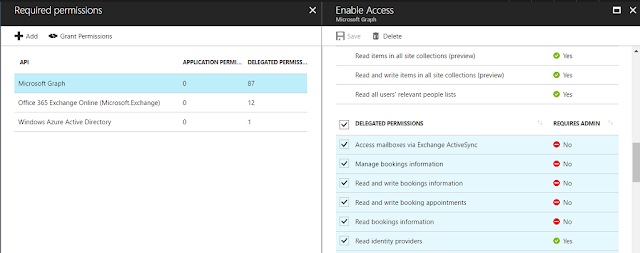
2. Then navigate to the required permissions option. Select the
required API and add the necessary permissions and save it. After saving, click
on grant permissions for enabling users to access the data.
3. Navigate to the reply URLs option and add your custom
application URLs. The reply URLs are used as callbacks. The tokens from the
Azure AD will be passed to the applications using query parameters in the reply
URLs.
On Azure AD, necessary permissions are given. Next, the custom applications can initiate the calls for authentications and access the data available on Microsoft services like graph API, outlook, calendars, etc. The following post describes one such authentication method to access the calendar events of user from outlook using graph API and outlook API.
The following Microsoft article describes more about authentication mechanisms using Azure AD.